Penetration Testing
We Are CREST Accredited

Recent data reveals that 29% of targets have at least one critical vulnerability, and 44% face the risk of one or more essential vulnerabilities. In light of these alarming figures, it is evident that penetration testing has evolved from a mere option to an absolute necessity across various sectors.
Penetration testing is an authorized simulated attack conducted on systems to assess their security. Penetration testers employ identical tools, techniques, and processes employed by malicious actors to identify and demonstrate the potential business impact stemming from vulnerabilities within the system. These assessments typically simulate various types of cyberattacks that could threaten an organization. While scrutinizing different system roles, they ascertain whether a system exhibits the resilience required to withstand attacks from authenticated and unauthenticated systems.

10 Tips For Choosing The Right Penetration Testing Service Firm
Tip 1: Methodology: Consider a pen testing firm with current knowledge and expertise in using the most recent pen test tools and techniques, demonstrated through Certifications, credentials, and adherence to standards.
Tip 2: Reporting: Evaluate the quality of the firm’s reports through samples and attestation letters to determine the depth and value of their testing. Reports should be comprehensive, concise, and identify vulnerabilities with actionable remediation recommendations.
CONDUCTED
RETENTION
Accorian is CREST Accredited
CREST, a result-driven accreditation, prioritizes delivering favorable outcomes that will enhance and safeguard our client’s interests when achieved. It demonstrates our ability to provide comprehensive and effective security testing services that meet the most stringent industry standards.
Why Choose Accorian?
Accorian elevates the penetration testing process by identifying vulnerabilities, offering actionable recommendations for remediation, and implementing compensatory controls. This unique capability enables us to prioritize and customize solutions aligned with various compliance requirements. We excel in providing clients with a comprehensive understanding of their overall security posture.
Accorian is
CREST Accredited
CREST, a result-driven accreditation, prioritizes delivering favorable outcomes that will enhance and safeguard our client’s interests when achieved. It demonstrates our ability to provide comprehensive and effective security testing services that meet the most stringent industry standards.
Why Choose Accorian?
Accorian elevates the penetration testing process by identifying vulnerabilities, offering actionable recommendations for remediation, and implementing compensatory controls. This unique capability enables us to prioritize and customize solutions aligned with various compliance requirements. We excel in providing clients with a comprehensive understanding of their overall security posture.
Why Do You Need Pentesting?
Penetration testing extends beyond the detection of common vulnerabilities through automated methods and instead identifies more intricate security issues, including business logic flaws and payment gateway complexities. It plays a pivotal role in enhancing understanding of the organization’s security posture and effectively addressing challenges to fortify security measures
The primary objectives of conducting regular penetration tests are:
- Staying vigilant and informed about the ever-evolving cyber threat landscape
- Detecting and rectifying business logic error
- Preparing for compliance audits effectively
- Protecting your organization's defenses against security breaches
Our Pentesting Services
- Red Team Exercises
- Phishing/Email Social Engineering
- Internal Penetration Testing
- Wireless Penetration Testing
- Application Penetration Test
- External Penetration Test
- Secure Code Review
Red Team Exercise
This comprehensive security assessment simulates real-world attacks on an organization’s security infrastructure, focusing on specific vulnerabilities. It takes a holistic approach, aiming to compromise the organization’s security posture. The red team comprises highly skilled security professionals who take on the role of attackers to assess the effectiveness of an organization’s defensive measures. They aim to uncover potential security gaps, demonstrating how attackers combine unrelated exploits to access sensitive data and critical assets. Following the assessment, the team provides recommendations and plans to bolster the organization’s security posture, ensuring it remains resilient in the face of evolving threats.
Phishing/Email Social Engineering
This is a significant cybersecurity threat as attackers deceive individuals into revealing sensitive information via deceptive emails or websites impersonating trusted entities. To combat this threat, our comprehensive approach includes expert-led phishing campaigns tracking open and click-through rates to assess risks. Furthermore, powered by a SaaS platform, we streamline advanced phishing simulations to fortify defenses and enable swift threat response. We also offer ongoing security awareness assessments through actionable insights and replicate advanced phishing attacks, including real-time phishing (MitM), to enhance realism and bolster defense against phishing threats.
Internal Penetration Testing
This proves instrumental in finding vulnerabilities in applications residing within a company’s firewall-protected environment. This process entails simulating a potential attack scenario, particularly one initiated by a malicious insider. By taking this proactive approach, we aim to identify and rectify these vulnerabilities and can help prevent the risk of an attack caused by either a rogue employee or an unauthorized individual exploiting stolen employee credentials.
Wireless Penetration Testing
This involves evaluating the security of wireless networks, which can serve as potential entry points for unauthorized access to internal assets. Our dedicated team conducts rigorous assessments of your wireless network security configurations, concentrating on potential threats linked to unauthorized access. Through meticulous examination, we identify vulnerabilities and gaps in your wireless security defenses that could be exploited. Subsequently, we offer a comprehensive evaluation report outlining our findings and specific recommendations to strengthen your wireless security measures seamlessly.
Application Penetration Testing
This is conducted on an application that reveals coding errors and permission-related issues that may result in a data breach. Our team of certified experts, who have undergone rigorous training and evaluation, possesses the expertise to identify these vulnerabilities across various programming languages and software environments.
External Penetration Testing
This is the most effective approach to identify vulnerabilities in a company’s internet-exposed IT assets, such as domain servers, websites, and email systems. Our security experts specialize in identifying and assessing these vulnerabilities, evaluating their potential for exploitation by malicious hackers.
Secure Code Review
This is vital in uncovering and rectifying critical vulnerabilities within your codebase, including those that might be concealed on the front end of your application. Accorian employs state-of-the-art tools and methodologies to conduct these scans, ensuring your application is released to production with a robust security posture, free from any significant weaknesses that malicious actors could exploit.
Penetration Testing Methodology
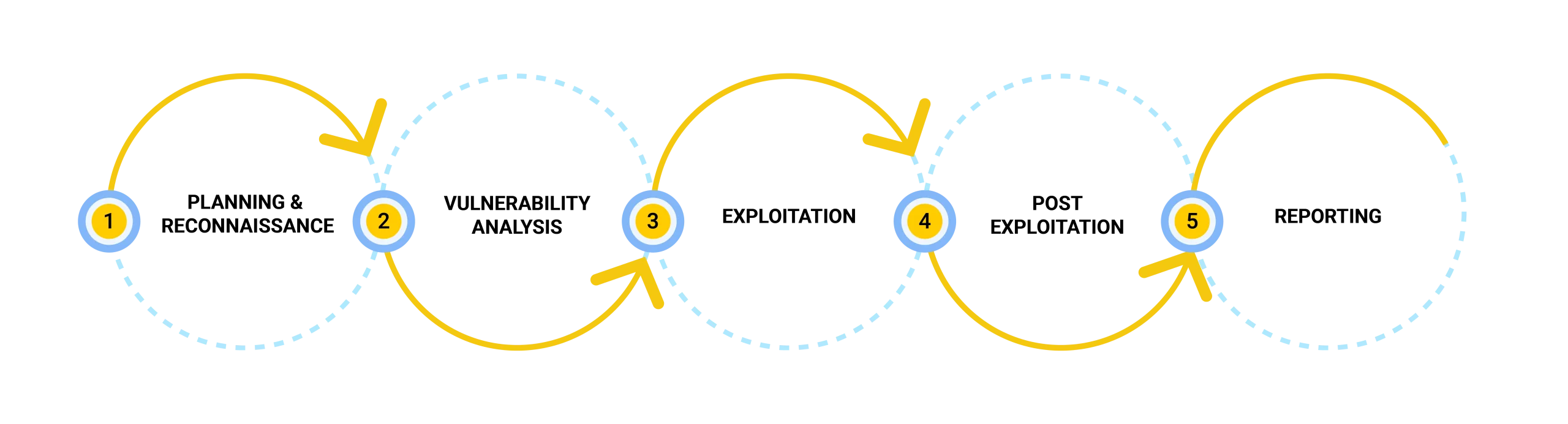
PenTesting Steps
Depending on the specifics of your situation, our pentesting procedure would include some or all of the following steps:
1
Planning & Reconnaissance
- Use passive techniques like searching online resources to gather information about the target system or network
- Use active techniques like port/service scanning and enumeration to identify potential weaknesses and develop test cases
- Traverse through the application to identify workflows and feature lists and develop test cases
2
Vulnerability Analysis
- Perform an automated scanning process to detect all easily identifiable findings
- Validate the vulnerablities identified by the scanner to eliminate false positives
- Conduct manual testing of the application/systems against all potential threats identified during the reconnaissance phase
3
Exploitation
- Leverage TTPs (Trctics, Techniques & Procedures), proprietary tools, & research to discover and analyze
- Exploit the identified vulnerabilities to evaluate their impact on the systems
- Traverse through the application to identify workflows and feature lists and develop test cases
4
Post Exploitation
- Remove all expoit files or payloads that have been uploaded or installed on the target system.
5
Reporting
- Prepare comprehensive reports tailored for technical and executive teams.
- Provide clear illustrations of identified vulnerabilities, including descriptions, mitigation strategies, & steps to reproduce.
- This will assist in verifying the implementation of appropriate measures to address the identified issues.
4 Pervasive Penetration Testing Methodologies
Accorian’s penetration testing approach combines our bespoke procedures, incorporating the highest standards, with industry-recognized techniques well-suited for businesses. This methodology outlines the meticulous planning and execution of a penetration test.
The four leading penetration testing approaches that are acknowledged and esteemed in the industry are:
-
OSSTMM
The Open Source Security
Testing Methodology Manual
-
OWASP
Open Web Application
Security Project
-
NIST
National Institute of Standards
& Technology
-
PTES
Penetration Testing
Execution Standard
Key Differentiators
We leverage our automated scanners & tools along with our custom scripts to conduct thorough assessments and ensure comprehensive coverage
Combined experience of working with 500+ clients on 1200+ penetration tests, detection of 25000+ vulnerabilities, & 100% success rate in red team engagements
A Trusted Vulnerability Assessor & an Approved Scan Vendor (ASV) for organizations in sectors such as bank financial services, credit unions, eCommerce, & SaaS that need to adhere to PCI DSS requirements
Our test plans aim to cover 200-400 checks for network penetration tests and 400-800 reviews for application penetration tests
Our time-tested and proven penetration testing methodology is built using OSSTMM, OWASP, NIST, & PTES standards
End-to-end project management for assessments with comprehensive & detailed reporting through our platform
Resources
CONSULTING & ASSESSMENT SERVICES
Office Address
Accorian Head Office
6,Alvin Ct, East Brunswick, NJ 08816 USA
Accorian Canada
Toronto
Accorian India
Ground Floor,11, Brigade Terraces, Cambridge Rd, Halasuru, Udani Layout, Bengaluru, Karnataka 560008, India
Ready to Start?
Senior Manager - Penetration Testing (5-7 years)
Penetration Tester Consultant (2-4 years)
Manager for Compliance Services (4- 6 yrs)
A day in the life
- Perform Penetration Testing for networks (internal & external), applications, APIs & cloud assets
along with Red & Purple Team assessments - Vulnerability identification and analysis
- Collaborate with team members and stakeholders to define project scopes, review test results,
and determine remediation steps - Draft reports and communicate complex security concepts and test findings to clients and
stakeholders - Make expert recommendations to help clients improve their information security program
- Work on researching & developing utilities, toolkits, processes, tactics, and techniques
Qualifications & Requirements
- 5-7 years of penetration testing experience, preferably in highly regulated industries and for
global clients - At least 2-3 years of experience in managing a team is a plus
- Proficiency with scripting and programming languages
- Advanced problem-solving skills
- OSCP/OSWE certification preferred but, GPEN, GWAPT, GXPN, CREST, CESG, and similar
certifications are a plus - Experience with Cobalt Strike a plus
- Strong written and verbal communication skills
- Ability to work autonomously with little directional oversight
- Ability to lead a project and multiple testers
- Commitment to quality and on-schedule delivery; and a proven ability to establish and meet
milestones and deadlines - Customer-focused mentality to understand and appropriately respond to customers’ business
needs
A day in the life
- Perform Penetration Testing for networks (internal & external), applications, APIs & cloud assets along with Red & Purple
Team assessments - Vulnerability identification and analysis
- Collaborate with team members and stakeholders to define project scopes, review test results,
and determine remediation steps - Draft reports and communicate complex security concepts and test findings to clients and
stakeholders - Make expert recommendations to help clients improve their information security program
- Work on researching & developing utilities, toolkits, processes, tactics, and techniques
Qualifications & Requirements
- 2-4 years of penetration testing experience, preferably in highly regulated industries and for global clients
- Proficiency with scripting and programming languages
- Advanced problem-solving skills
- OSCP certification preferred but, GPEN, GWAPT, GXPN, CREST, CESG and similar certifications a plus
- Experience with Cobalt Strike a plus
- Strong written and verbal communication skills
- Ability to work autonomously with little directional oversight
- Ability to lead a project and multiple testers
- Commitment to quality and on-schedule delivery; and a proven ability to establish and meet milestones and deadlines
- Customer-focused mentality to understand and appropriately respond to customers’ business needs
JD for Compliance Services
Accorian is an emerging well-funded cybersecurity strategy consulting start-up with a global clientele
and headquartered in New Jersey with regional offices in UAE & India. Our team comprises of
cybersecurity & IT industry veterans who’ve held leadership & CXO roles at large global enterprises.
We help secure disruptors & technology first companies in the US who are trailblazers in their own
fields & will emerge as the next unicorn of the world. Our clients range from FinTechs, HealthTechs,
MSPs, SaaS etc.
Benefits include best in class salaries, bonuses, family insurance, exposure to global clients working
on the next gen technologies, working with a team with an average experience of 15+ years in
technology & security and overall experience of conducting 100s of audits, assessments, trainings,
labs etc.
A day in the life
- Aid our clients in implementing & meeting various standards, regulatory and
compliance requirements such as SOC 2, HIPAA, HITRUST, NIST CSF, ISO27001 etc. - Assist senior members of the team with assessments and audits
- Ensures the effectiveness of the IT compliance and security program & assist in
developing and executing mitigation plans - You will aid our clients to meeting various standards by –
- Enhancing the client’s understanding of the standard by breaking down the
requirement statements, tasks & specifications - Facilitate/conduct activities like Risk Assessment, Control Testing, Pre-audit/Internal
Audit - Program Manage for successfully implementing the standard/s
- Design Policies & Procedures and Security Controls
- Provide expert opinion on mandatory tools and technologies
- Prepare Technical designs & business case studies for various IT security technologies &
products. - Conduct audits/assessments including audit plan preparation, review of
documentation & evidence, evaluation of procedures, and client interviews - Manage priorities and tasks to achieve delivery utilization targets
Qualification / Requirement
- Relevant experience in compliance services
- Security Certification
- Advanced problem-solving skills & attention to detail
- Strong written and verbal communication skills
- Ability to work autonomously with little directional oversight
- Ability to lead a project and multiple consultants & client resources
- Commitment to quality and on-schedule delivery
- Customer-focused mentality to understand and appropriately respond to customers’ business needs
Drop your CVs to joinourteam@accorian.com
Interested Position




