In today’s healthcare environment, financial operations are inseparable from data security. While Revenue Cycle Management (RCM) forms the financial backbone of healthcare, spanning the entire patient journey, it also necessitates the handling of Protected Health Information (PHI), making HIPAA compliance critical to safeguarding patient privacy and ensuring financial integrity.
Healthcare organizations face mounting pressure to ensure that their RCM workflows not only optimize reimbursement but also comply with HIPAA’s Privacy, Security, Breach Notification, and Omnibus Rules. Accorian helps bridge this gap by embedding security and compliance into financial operations, assuring that every transaction, system, and vendor relationship meets regulatory standards without compromising efficiency. In a digitized ecosystem, aligning RCM with HIPAA is not just about avoiding fines; it’s about safeguarding revenue streams and maintaining patient trust.
Why Financial Operations Must Align with Data Security
Failure to embed security controls into RCM workflows exposes healthcare entities to dual risks: regulatory penalties for PHI violations and financial leakage through claim denials, coding errors, or fraud. In a digitized ecosystem, ensuring HIPAA compliance within RCM is not just about avoiding fines; it is about safeguarding revenue streams and maintaining patient trust.
Key HIPAA Rules Impacting RCM
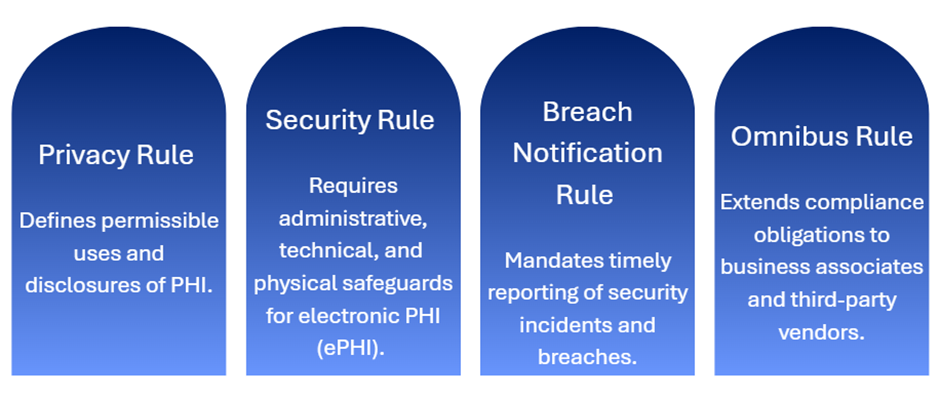
These rules, when applied to RCM, demand strict control over access rights, encryption of financial data, secured claims transmission, and transparent audit trails.
Embedding Compliance into High-Volume RCM Workflows
Healthcare billing generates tens of thousands of transactions daily, from prior authorization responses and claim edits to denial codes and remittance updates. Traditional manual reviews cannot scale to this volume, often missing coding discrepancies, unencrypted transmissions, or unauthorized data exposure.
CombineHealth’s AI-powered healthcare RCM platform illustrates how automation can bridge this gap by:
- Encrypting all transactions with AES-256 and enforcing role-based access controls.
- Integrating SOC 2-aligned logging to generate continuous evidence for audits.
- Applying triple-layer quality assurance through AI confidence scoring, peer-model validation, and certified coder reviews.
This model transforms compliance from a reactive checkbox activity into a live, embedded control mechanism that enforces HIPAA safeguards across every financial interaction.
Common Compliance Pitfalls in RCM

Left unchecked, these issues can expose organizations to HIPAA violations, payment delays, reputational damage, and costly remediation efforts.
10 Tips to Ensure Cybersecurity Compliance in RCM
Aligning financial operations with data security standards requires more than policy; it demands actionable practices. Healthcare organizations can strengthen both compliance and operational resilience by following these key steps:
- Embed HIPAA Safeguards – Integrate privacy and security requirements into every RCM workflow.
- Strengthen Access Controls – Enforce role-based access and multi-factor authentication.
- Encrypt Data End-to-End – Protect PHI in transit and at rest with strong encryption.
- Run Regular Risk Assessments – Identify gaps in billing systems and third-party integrations.
- Secure Vendor Relationships – Update BAAs and monitor third-party security posture.
- Automate Compliance Monitoring – Use GRC platforms to track controls and collect audit evidence.
- Maintain Detailed Audit Trails – Log every PHI-related transaction for accountability.
- Educate Staff Continuously – Train billing and financial teams on HIPAA and data security.
- Test Systems Frequently – Conduct penetration testing and vulnerability scans on RCM platforms.
- Leverage AI Oversight – Deploy AI tools to detect anomalies and enforce compliance at scale.
By embedding these practices, healthcare organizations can ensure their revenue cycle processes remain both financially efficient and fully compliant with data security mandates.
The Accorian Advantage
Is your organization ready to navigate compliance, protect sensitive data, and stay ahead of evolving cybersecurity threats? Accorian partners with healthcare providers, payers, and health tech platforms to strengthen security and compliance through an integrated suite of services.
From HIPAA and HITRUST readiness, covering risk assessments, gap analysis, and audit preparation, to penetration testing and security reviews across applications, cloud environments, infrastructure, and AI chatbots, Accorian ensures vulnerabilities are identified and mitigated before they impact operations.
Accorian also enhances third-party risk management through vendor assessments, BAA reviews, and managed programs. Its expertise spans SOC 2, ISO 27001, and AI security, powered by its GRC platform, GORICO. By uniting compliance, security testing, and continuous monitoring, Accorian ensures RCM and healthcare operations remain fully compliant, resilient, and growth-ready.
FAQs
Why does RCM need HIPAA compliance?
RCM (Revenue Cycle Management) handles patient data, so HIPAA compliance is needed to keep this information safe and private.
What happens if RCM isn’t secure?
Hospitals can face fines, lose money from errors or fraud, and damage patient trust.
Which HIPAA rules matter most for RCM?
The Privacy, Security, Breach Notification, and Omnibus rules are the most relevant.
How does technology enhance cybersecurity in RCM?
Technology enhances cybersecurity in RCM by protecting PHI with encryption, enforcing access controls, monitoring transactions in real time, and detecting vulnerabilities before they turn into breaches.
How can Accorian support us?
Accorian secures RCM workflows, manages vendor risks, and ensures full compliance with regulations.



